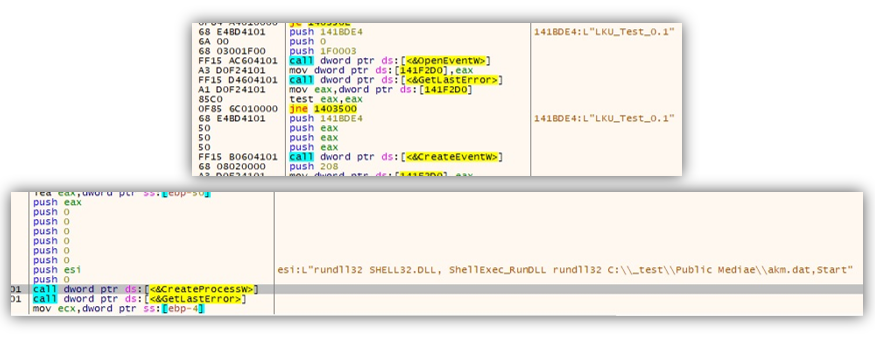
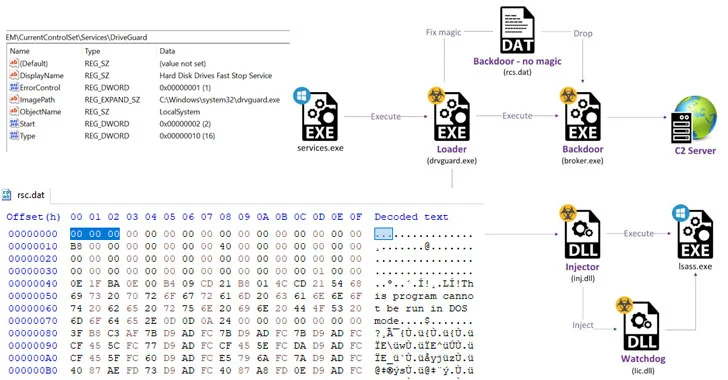
![Blue Team-System Live Analysis [Part 11]- Windows: User Account Forensics- NTUSER.DAT Rules, Tools, Structure, and Dirty Hives! | by Cyber Meisam [CM] | Medium Blue Team-System Live Analysis [Part 11]- Windows: User Account Forensics- NTUSER.DAT Rules, Tools, Structure, and Dirty Hives! | by Cyber Meisam [CM] | Medium](https://miro.medium.com/v2/resize:fit:628/1*8NzZPMe4CjydrpkGPXY_4g.png)
Blue Team-System Live Analysis [Part 11]- Windows: User Account Forensics- NTUSER.DAT Rules, Tools, Structure, and Dirty Hives! | by Cyber Meisam [CM] | Medium

Acronis Cyber Protect Cloud, Acronis Cyber Protect 15 and Acronis Cyber Backup 12.5: Connection Verification Tool - CVT | Knowledge Base

start.me - your personal start page on X: "Explore nixintel's curated #OSINT collection! Discover tools for popular platforms like Twitter, Instagram, YouTube, as well as specialized tools for Network Investigations, Google Dorks +

How to fix sound problem on any android phone | হঠাৎ করে মোবাইলের সাউন্ড কমে যায়? | By Mahbubur Rahman | Everyone is welcome to our today's episode. Been facing a lot













-png.png)