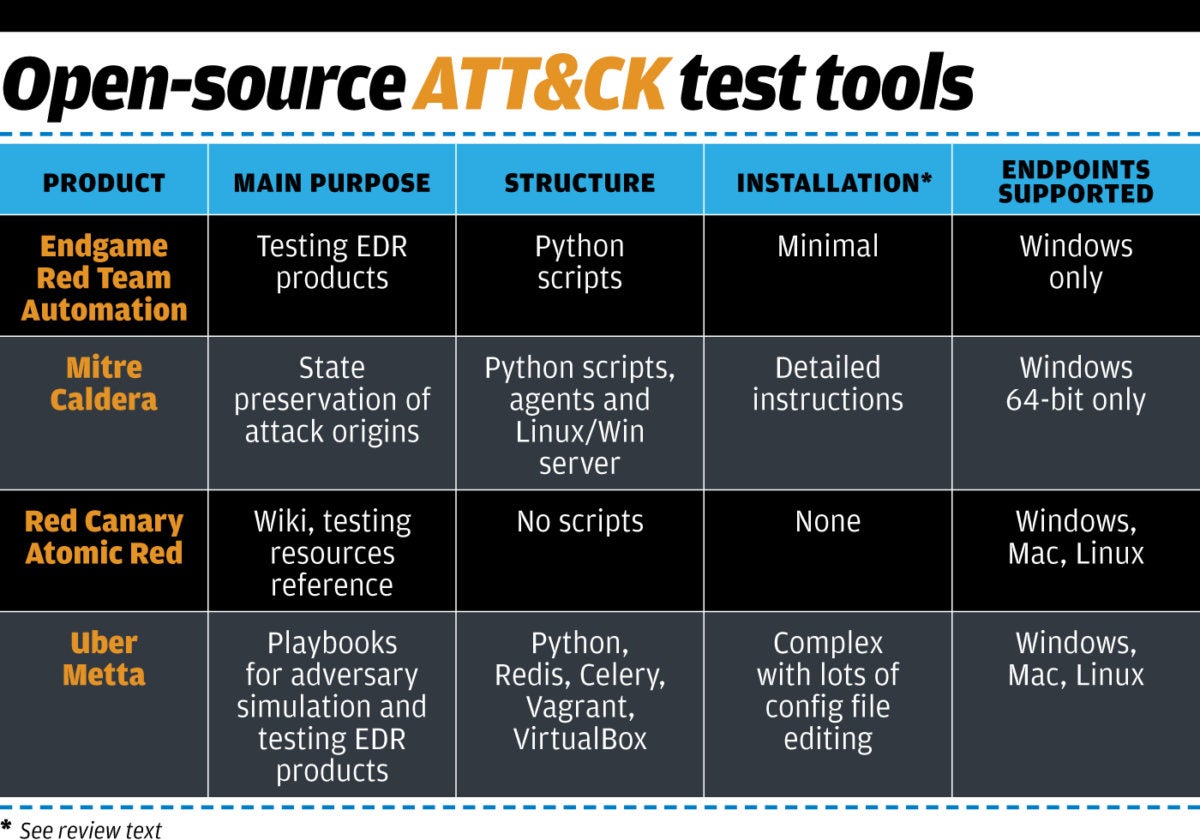
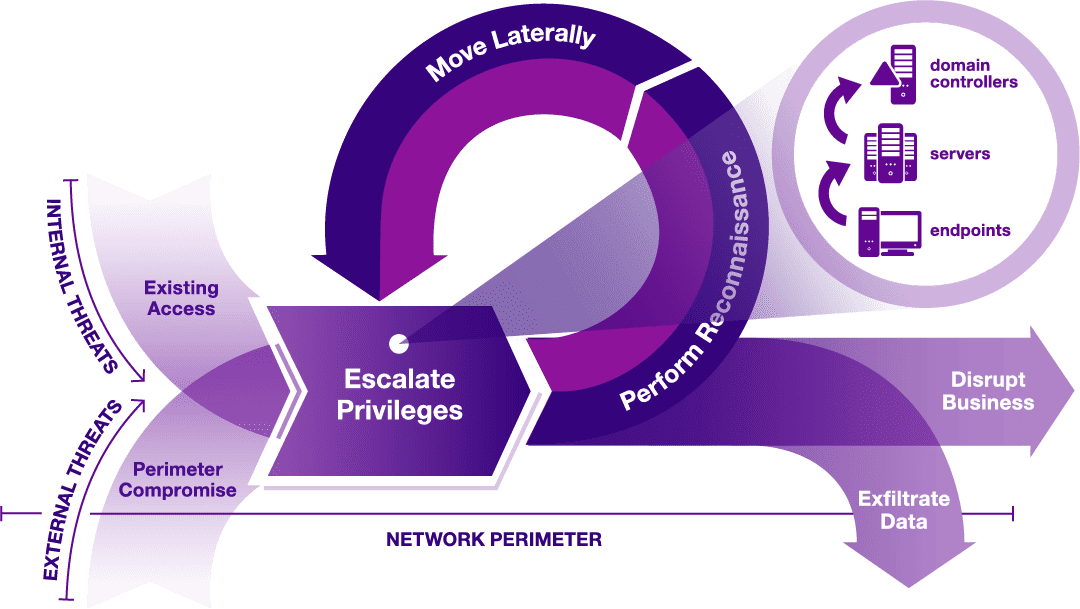
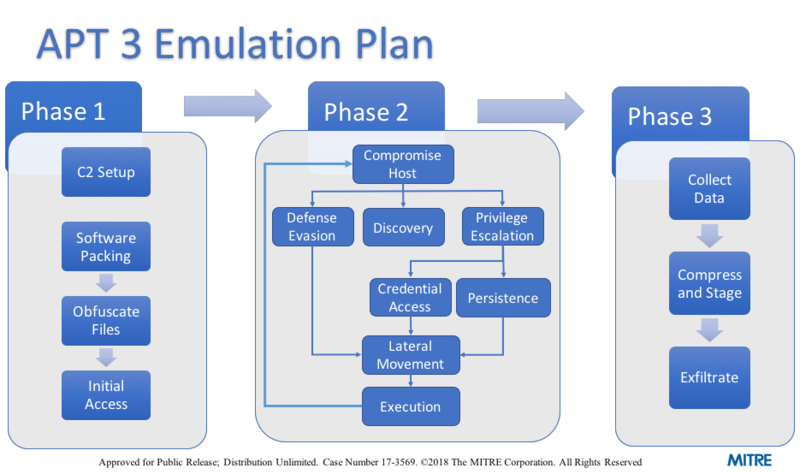
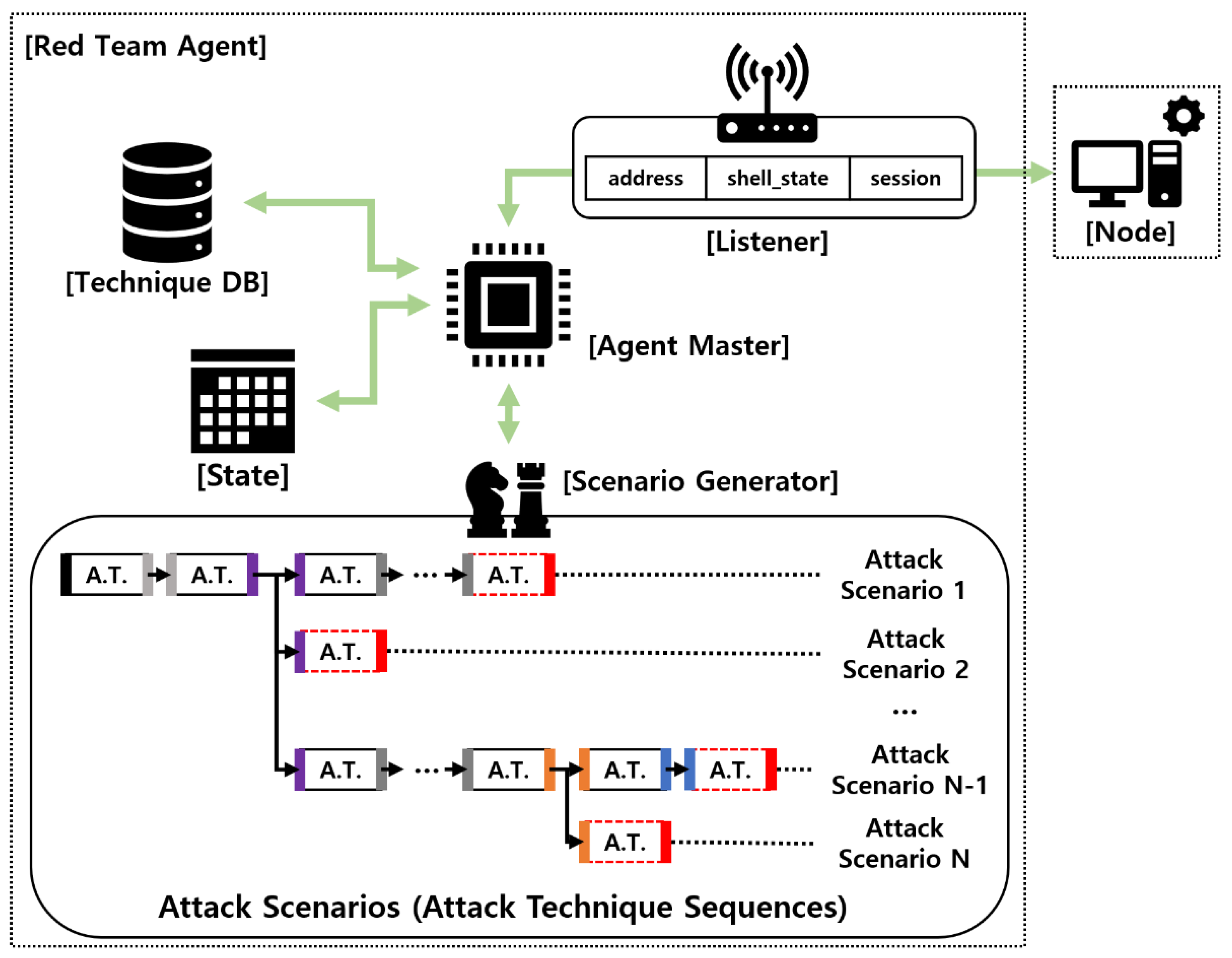
Leveraging Adversary Emulation / Simulation to Improve Security Posture in Organization | by Digit Oktavianto | MII Cyber Security Consulting Services | Medium

Christophe Tafani-Dereeper on X: "📢 Today, I'm thrilled to announce "Stratus Red Team", an open-source adversary emulation tool for the cloud! Comes with a catalog of cloud-native attack techniques that you can