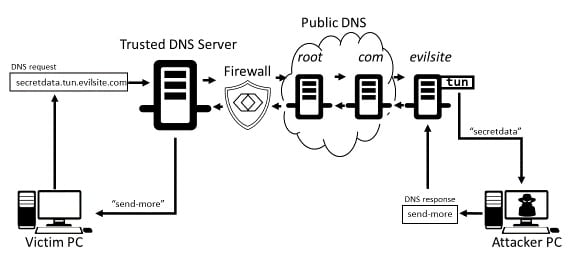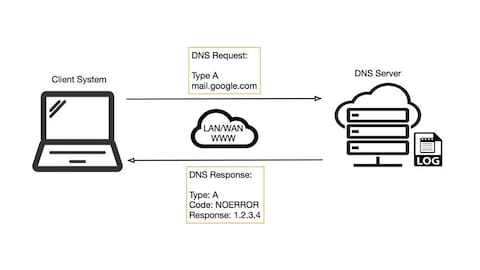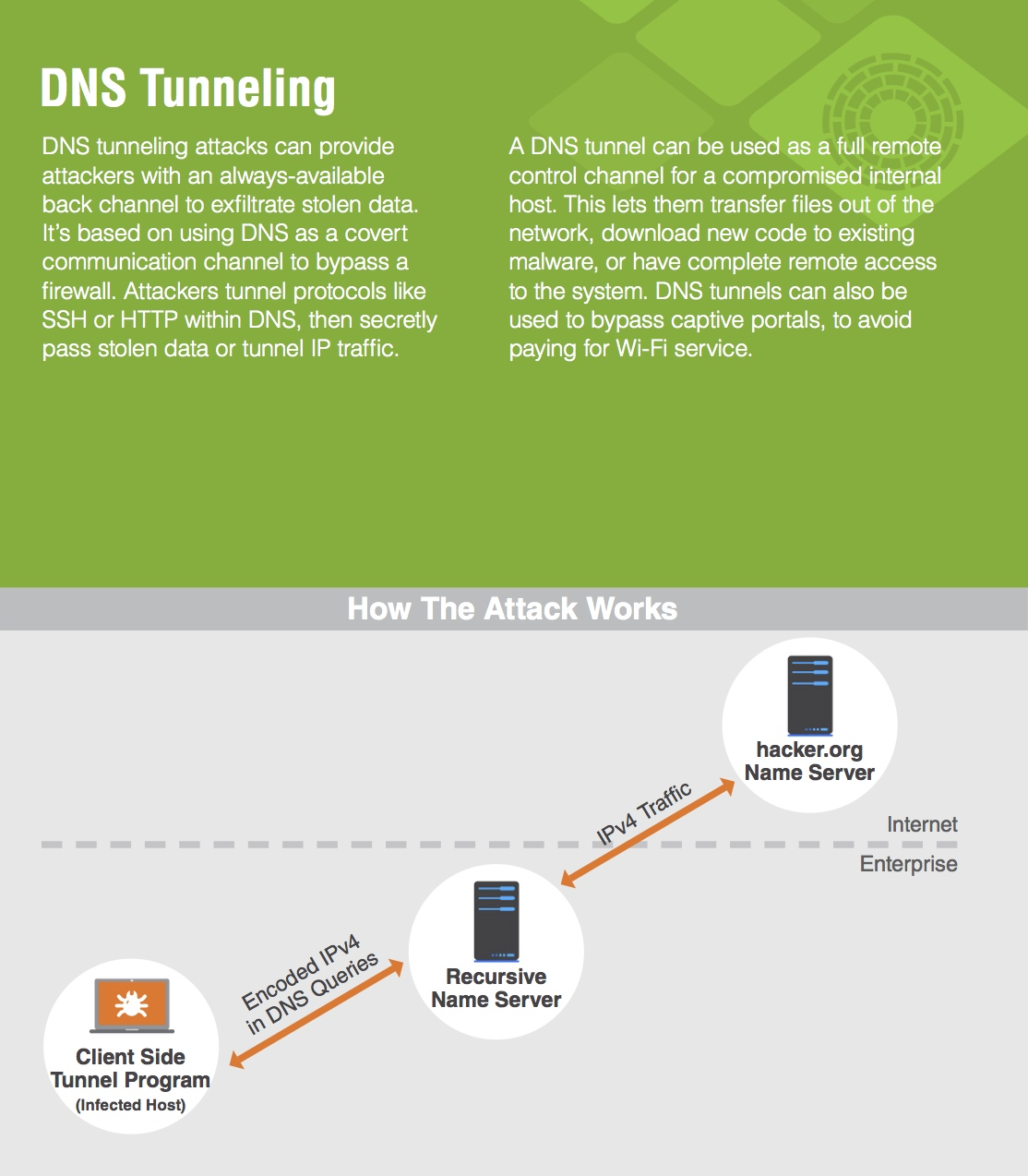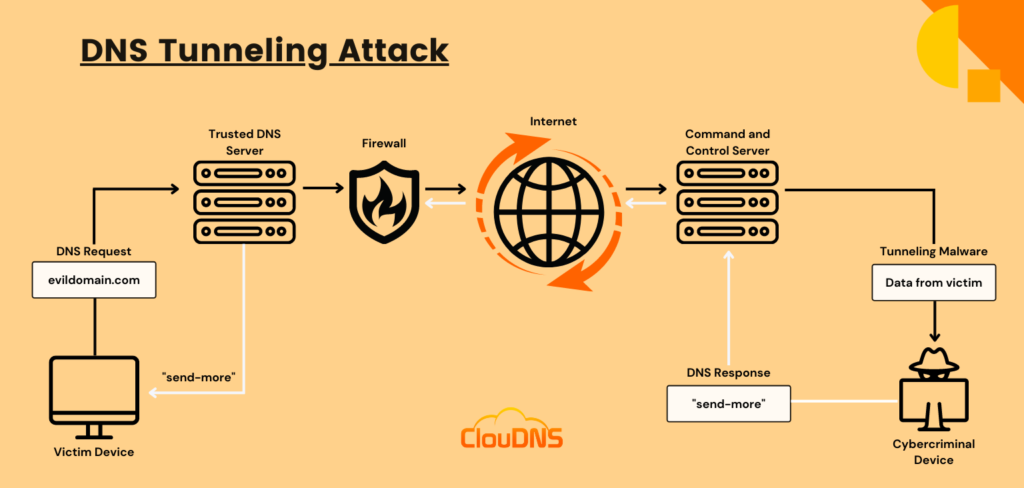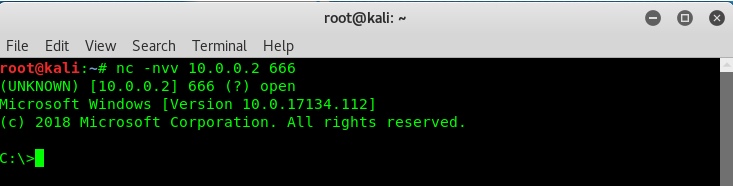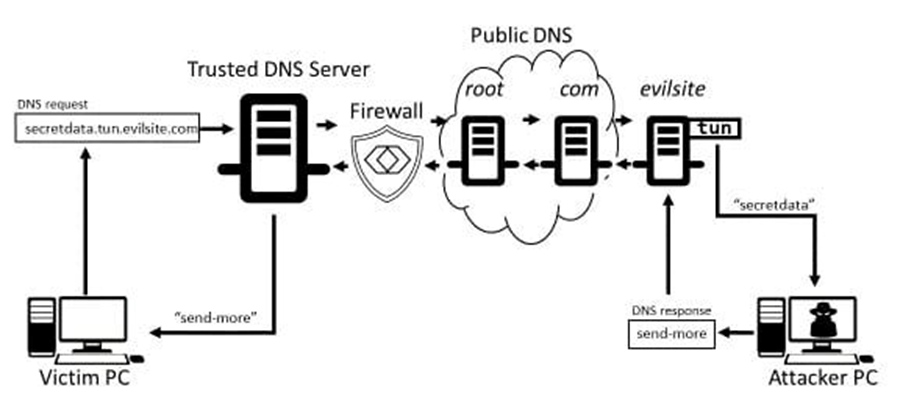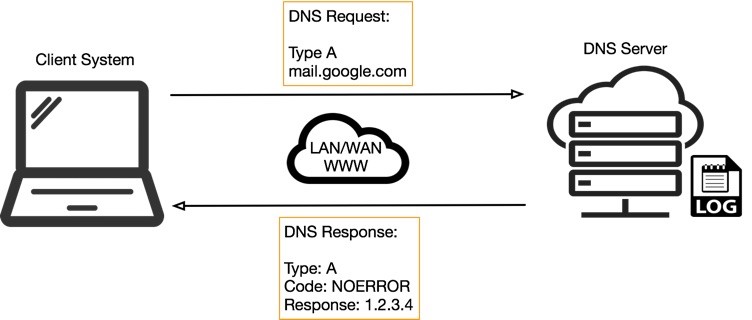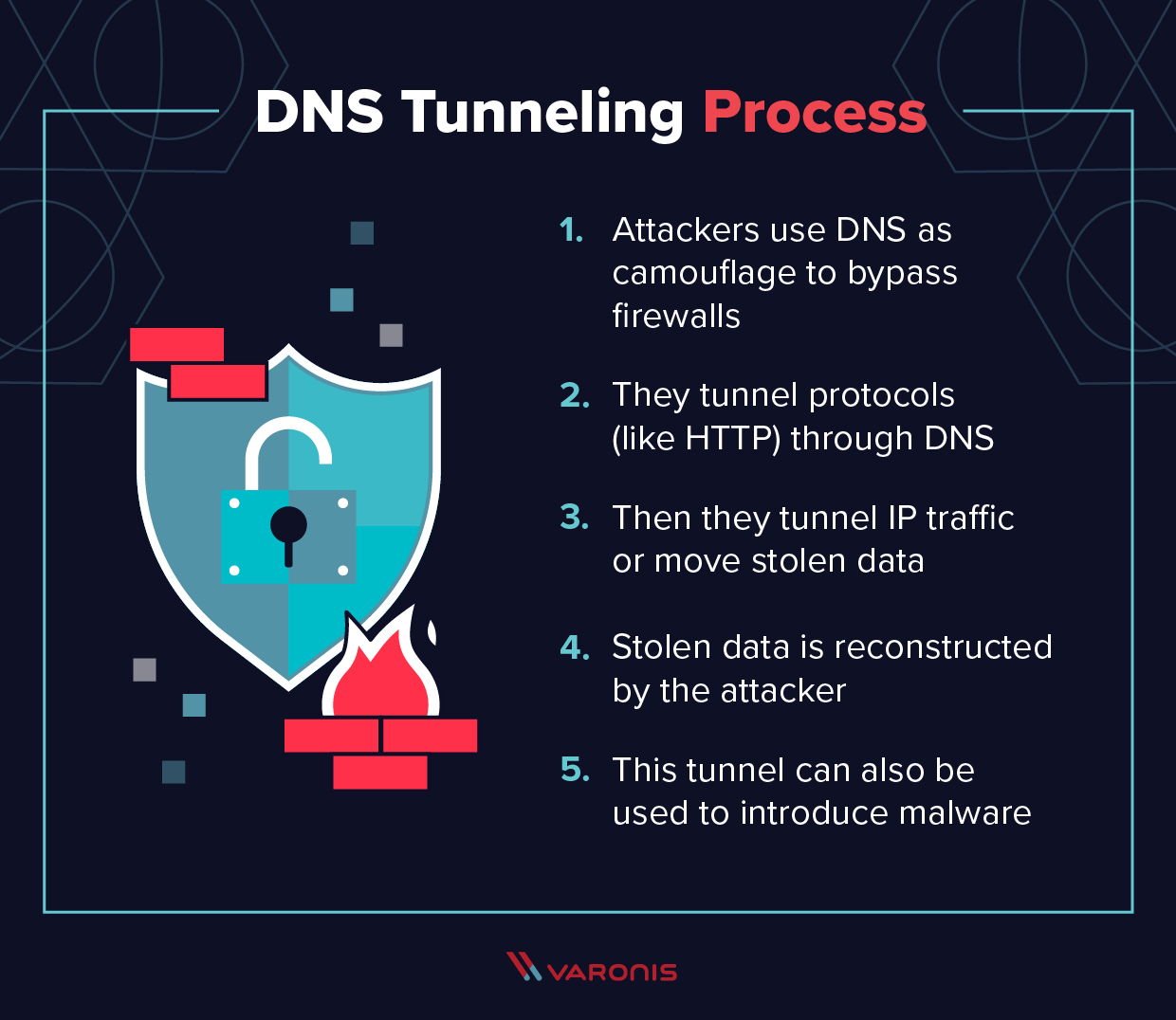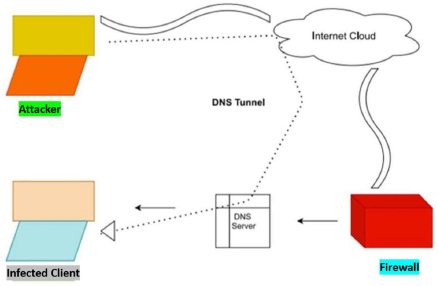
Advance Approach for Detection of DNS Tunneling Attack from Network Packets Using Deep Learning Algorithms
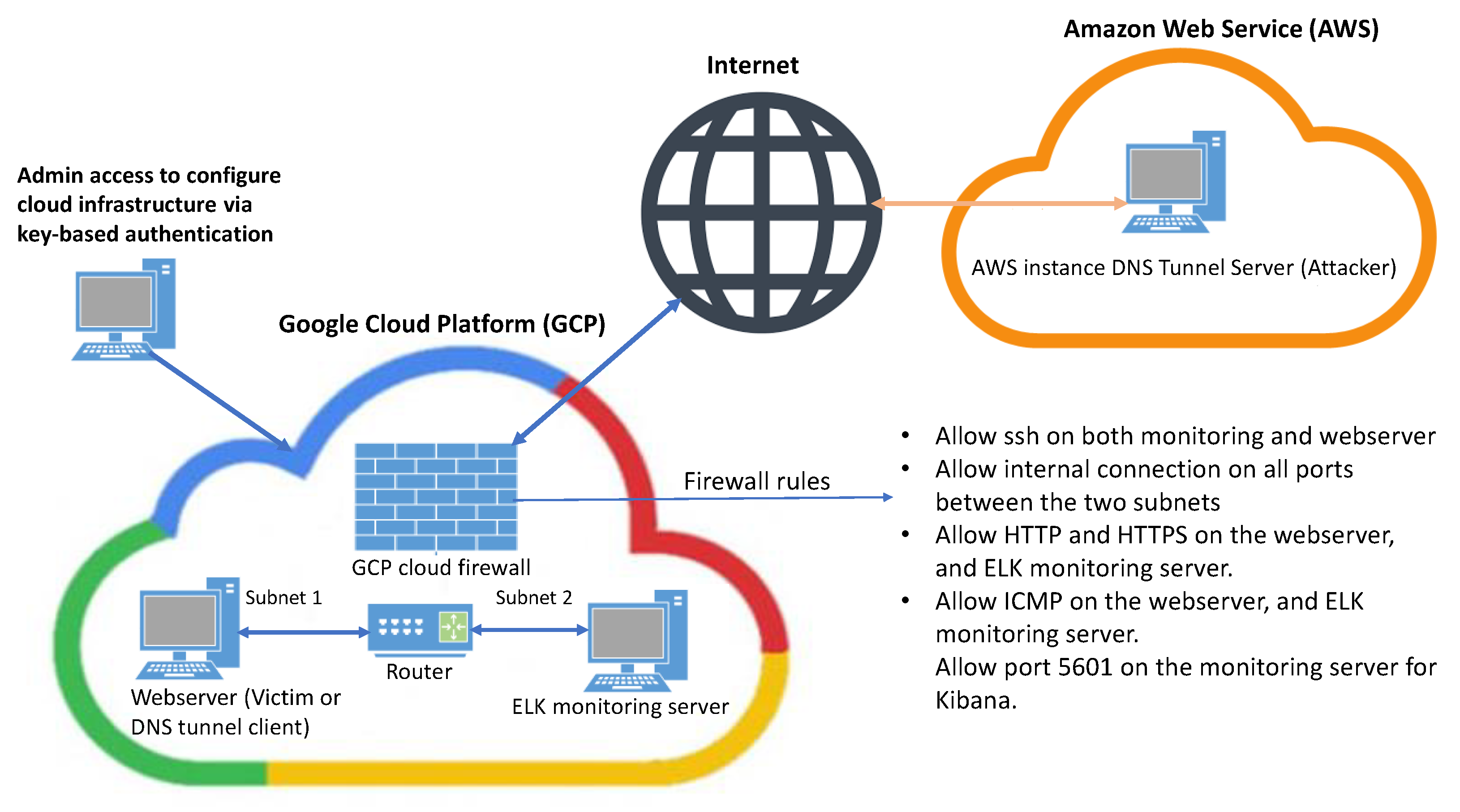
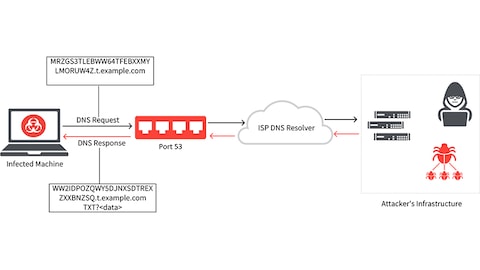
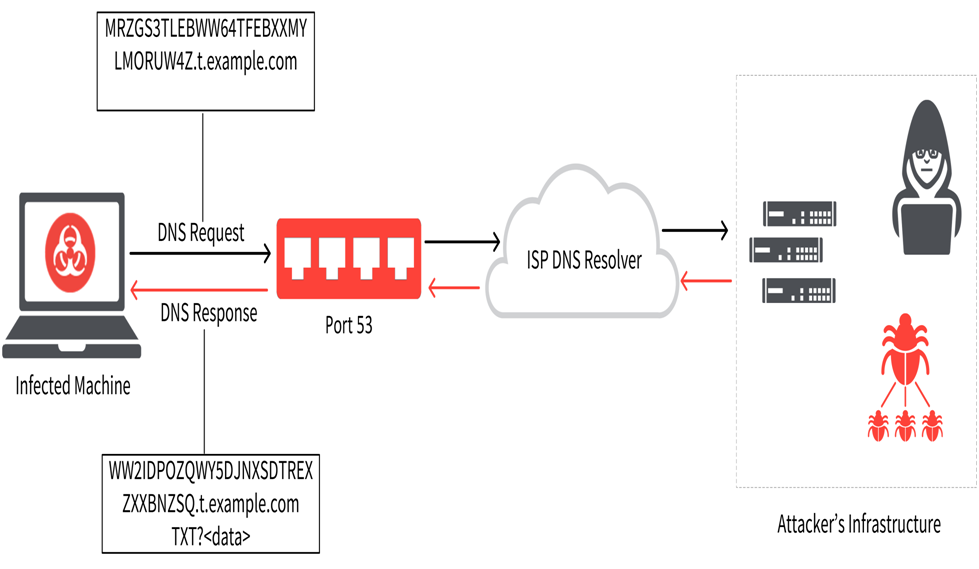
DNS Tunneling Simulation Topology 3.1. Log aggregation and simulation.... | Download Scientific Diagram
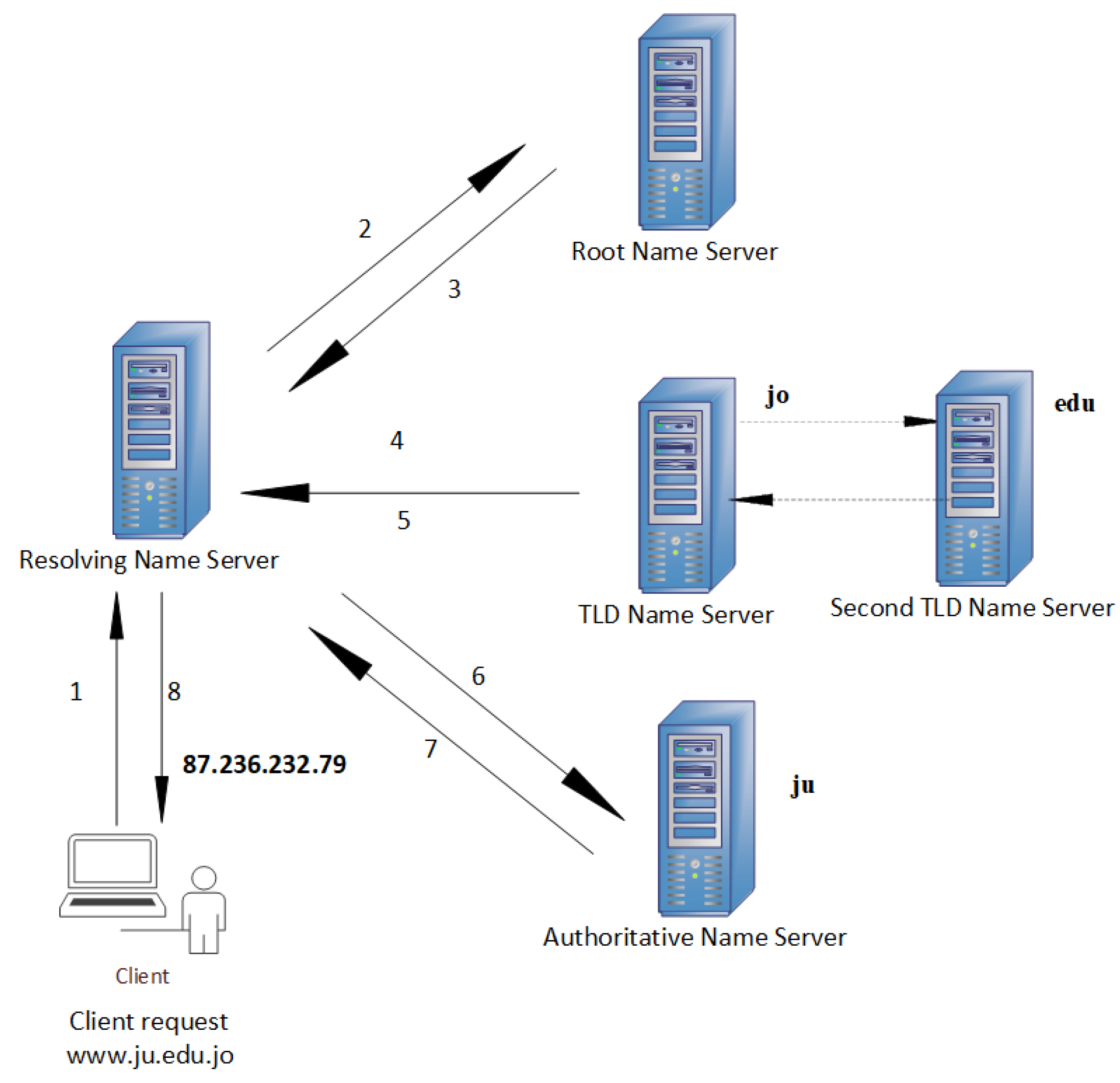
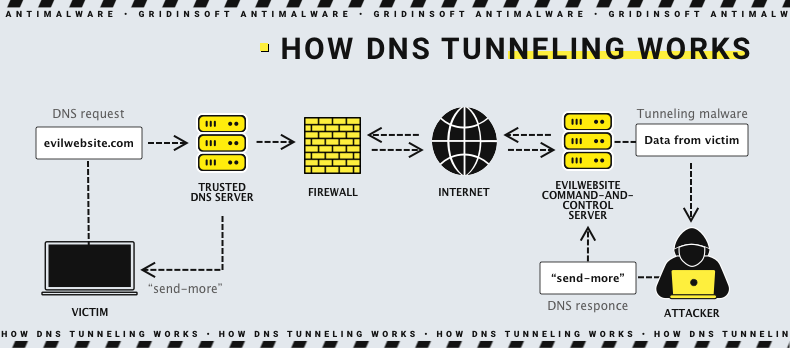
Electronics | Free Full-Text | Real-Time Detection System for Data Exfiltration over DNS Tunneling Using Machine Learning

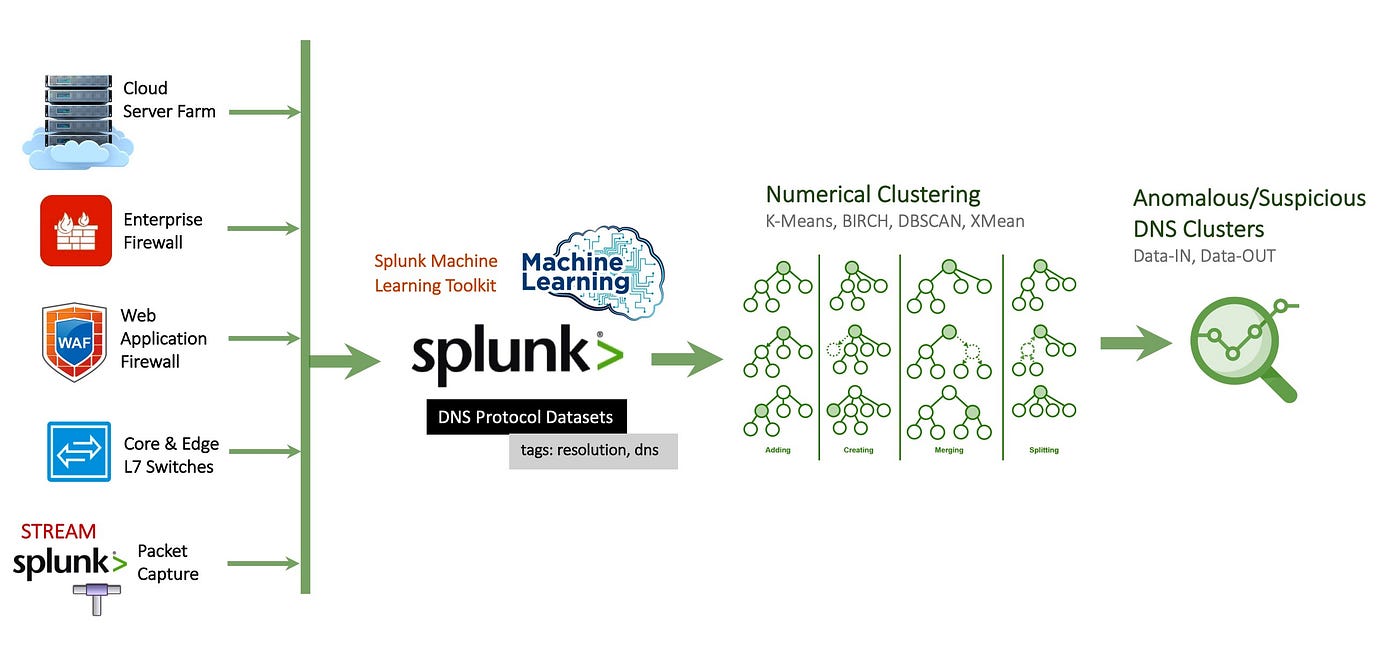
Identifying Malicious DNS Tunnel Tools from DoH Traffic Using Hierarchical Machine Learning Classification | SpringerLink