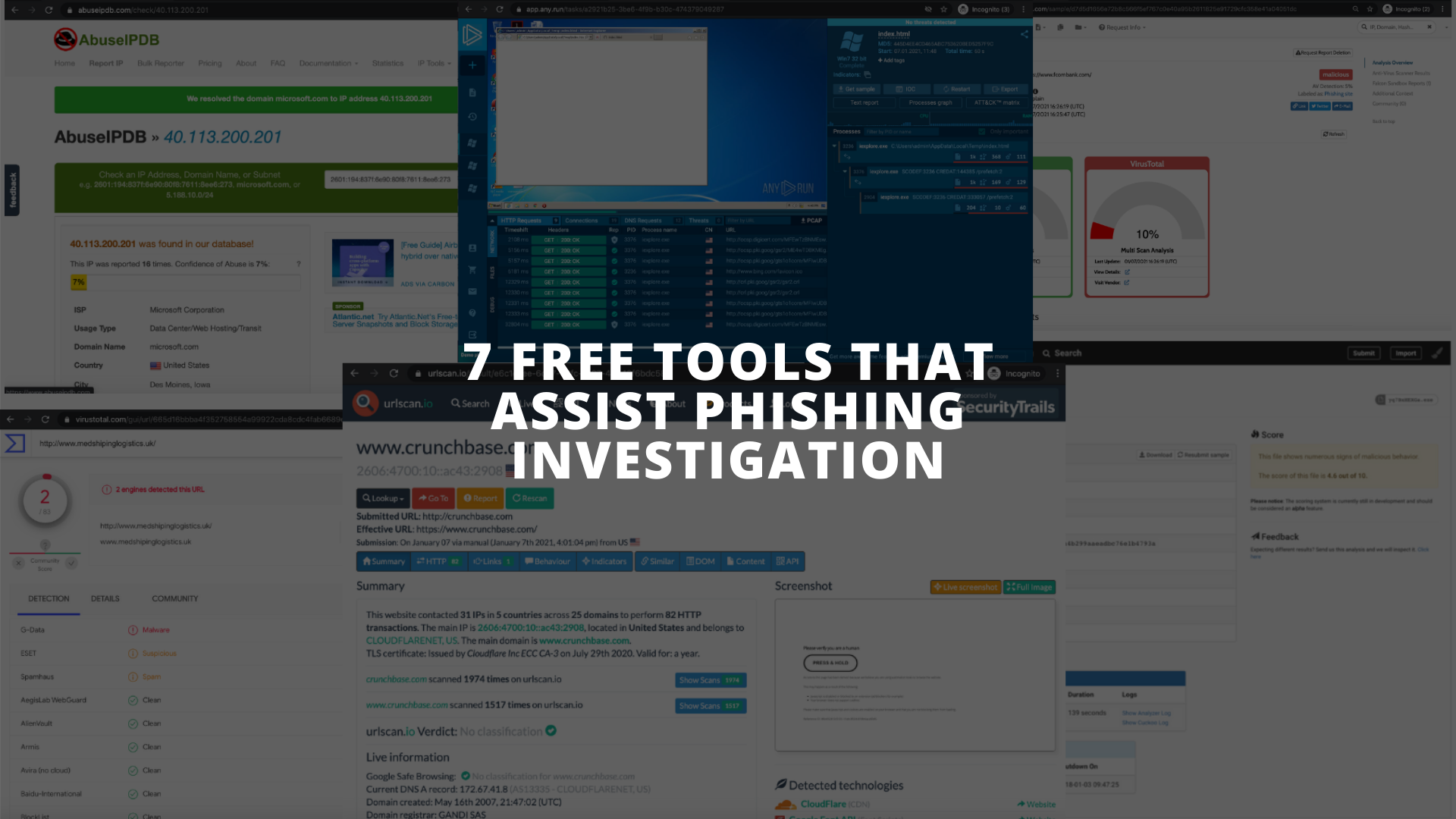
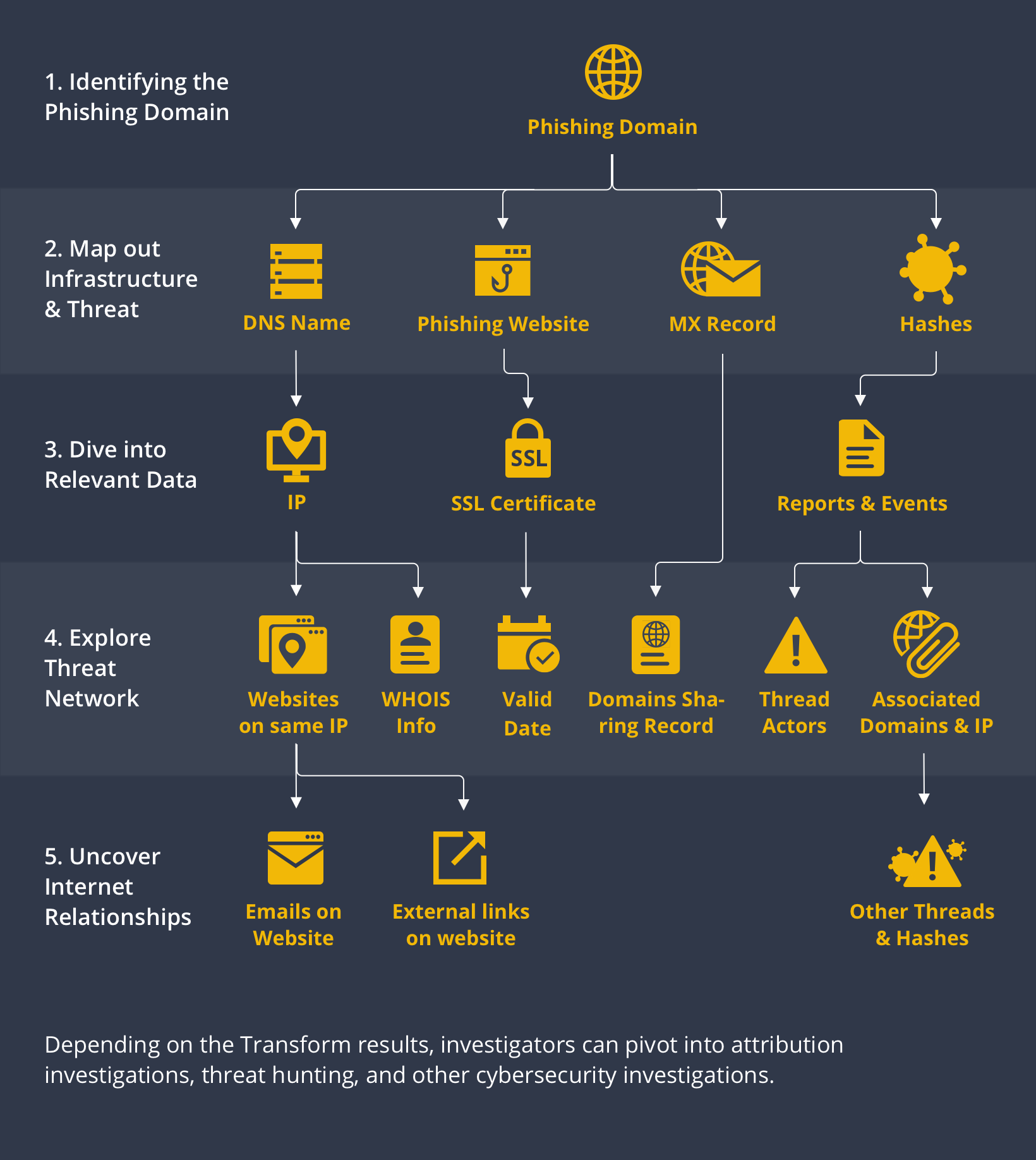
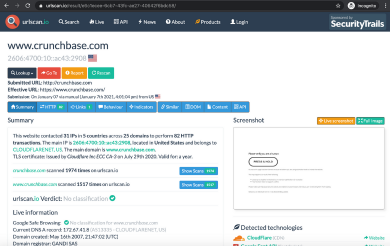
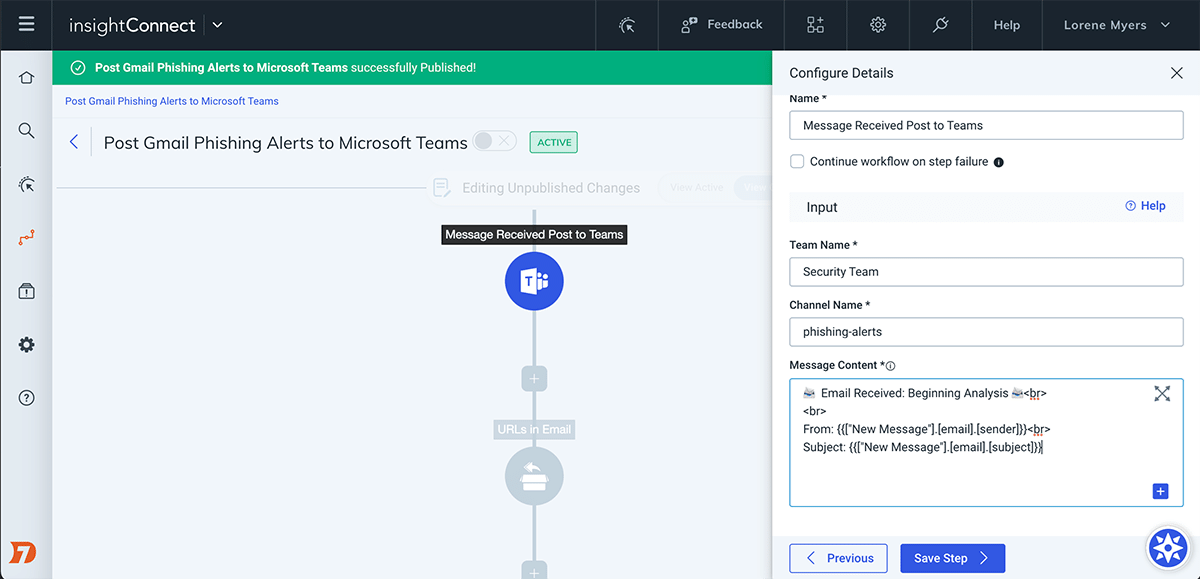
![PDF] Performance Analysis of Anti-Phishing Tools and Study of Classification Data Mining Algorithms for a Novel Anti-Phishing System | Semantic Scholar PDF] Performance Analysis of Anti-Phishing Tools and Study of Classification Data Mining Algorithms for a Novel Anti-Phishing System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/331bb7717f236ef1439ae66432b7b47f668918c5/6-Figure1-1.png)
PDF] Performance Analysis of Anti-Phishing Tools and Study of Classification Data Mining Algorithms for a Novel Anti-Phishing System | Semantic Scholar

From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud | Microsoft Security Blog

Group-IB: the use of phishing kits surges by 25% in 2022 as they become more evasive and advanced | Group-IB